SSDP attack#
A Simple Service Discovery Protocol (SSDP) attack is a reflection-based distributed denial-of-service (DDoS) attack that exploits Universal Plug and Play (UPnP) networking protocols in order to send an amplified amount of traffic to a targeted victim, overwhelming the target’s infrastructure and taking their web resource offline.
Here is a free tool to check to see if your public IP has any exposed SSDP devices: check SSDP DDoS vulnerability.
How this work?#
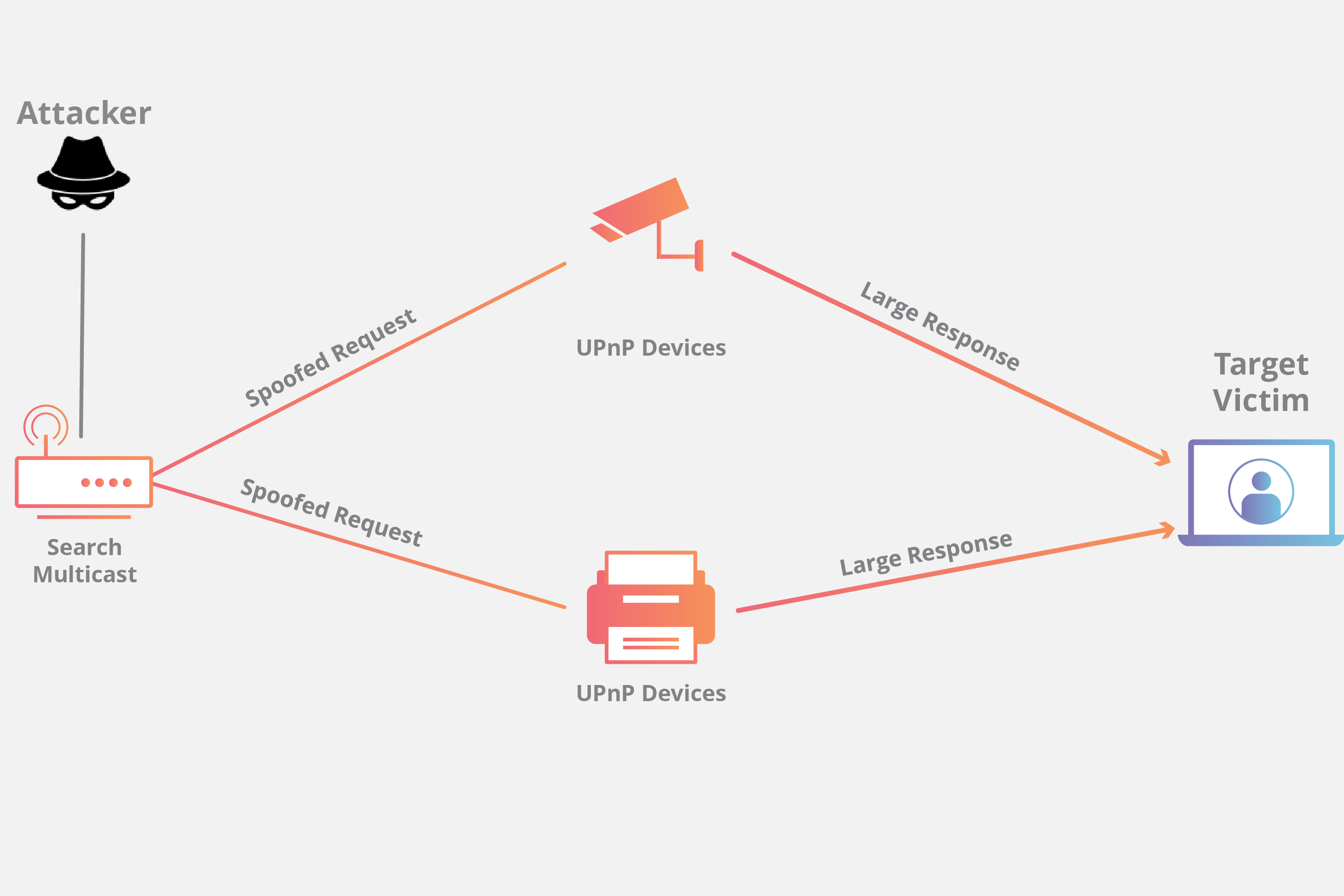
Under normal circumstances, the SSDP protocol is used to allow UPnP devices to broadcast their existence to other devices on the network. For example, when a UPnP printer is connected to a typical network, after it receives an IP address, the printer is able to advertise its services to computers on the network by sending a message to a special IP address called a multicast address. The multicast address then tells all the computers on the network about the new printer. Once a computer hears the discovery message about the printer, it makes a request to the printer for a complete description of its services. The printer then responds directly to that computer with a complete list of everything it has to offer. An SSDP attack exploits that final request for services by asking the device to respond to the targeted victim.
SSDP in 6 steps:#
First the attacker conducts a scan looking for plug-and-play devices that can be utilized as amplification factors.
As the attacker discovers networked devices, they create a list of all the devices that respond.
The attacker creates a UDP packet with the spoofed IP address of the targeted victim.
The attacker then uses a botnet to send a spoofed discovery packet to each plug-and-play device with a request for as much data as possible by setting certain flags, specifically ssdp:rootdevice or ssdp:all.
As a result, each device will send a reply to the targeted victim with an amount of data up to about 30 times larger than the attacker’s request.
The target then receives a large volume of traffic from all the devices and becomes overwhelmed, potentially resulting in denial-of-service to legitimate traffic.
